how to log a data breach
Set up a fraud alert or credit freeze. Cyber insurance can also help companies before an event takes place by helping supply the companies with.

Preventing Audit Log Data Breaches With Data Masking And Graph Deep Link Analytics Tigergraph
Subsequently have frameworks set up to help distinguish and contain breaks.
. The first step of the investigation of data breach is to determine the. Below are the best practices to follow to prevent data breaches. Communications services security breach PECR.
Ask your forensics experts and law enforcement when it is reasonable to resume regular operations. You can usually also log out those devices from these settings. Data breaches are a reality and its something that businesses need to be prepared for.
The log should describe the incident. A breach of security leading to accidental or unlawful destruction loss alteration unauthorised disclosure of or access to personal data. The quicker a Data breach can be identified and dealt with the lower the expense.
The average cost of a data breach in 2022 was 42 million 38 million The cost of a. An email data breach can happen when there are security issues with an email. Data Breach Incident Log Template.
GDPR requires all firms to keep a log of any and all breaches even the smallest incidents should be recorded. Instead try using an authenticator app like Google Authenticator or Okta. Types Of Data Breach.
Meaning cybercriminals can gain access to your information through an organisation website. Mobilize your breach response team right away to prevent additional data loss. In the GDPR a personal data breach is defined as a breach of security that results in the accidental or unlawful destruction loss alteration unauthorised disclosure of or access.
Some online services allow you to view what devices have recently used your login details and any recent transactions. The covered entity may report all of its breaches affecting fewer than 500 individuals on one date but the covered entity must complete a separate notice for each breach incident. Sending personal data to an incorrect recipient.
Credit and financial theft is the biggest target for identity thieves. The only thing worse than a data breach is multiple data breaches. Deliberate or accidental action or inaction by a controller or processor.
Instructions to Report A Data. Identify the Data Breach. Computing devices containing personal data being lost or stolen.
In the subject line of the email please include the following information. Educate and train your employees- Employees might be a weak link in the data security chain and of-course human. However there are 7 phases that you should follow for data security breaches.
Technically a data breach is a violation of security protocol for an organization or individual in which confidential information is copied transmitted viewed and stolen by an. Heres a look at some of the most common types of data. Whether the breach you wish to notify DPC of is new or an update to a previous breach notification.
The Cost of Data Breaches report presents the evidence for the impact of a data breach.

Healthcare Data Breach Leads To Prison Time Class Action Lawsuit Otava
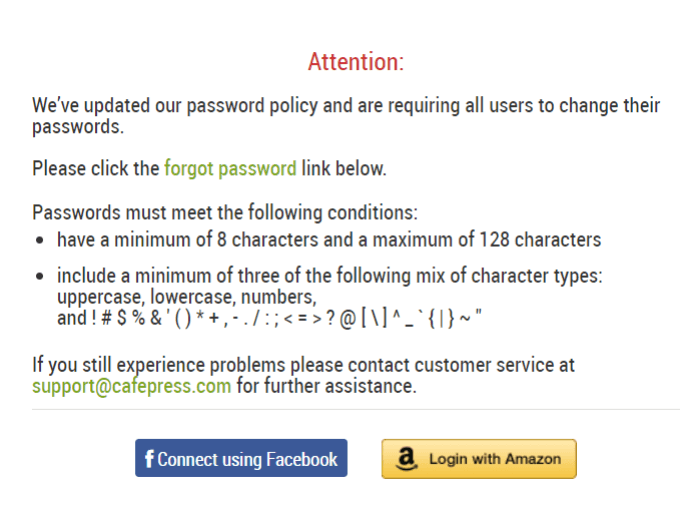
Cafepress Data Breach Exposes Personal Data Of 23 Million Customers
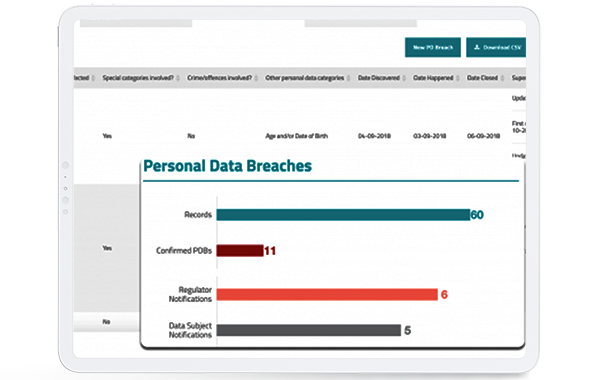
Data Breach Module The Product Keepabl Keepabl Tm

Log Management Digital Forensics In Data Protection

4 Steps To Planning A Successful Data Breach Incident Response
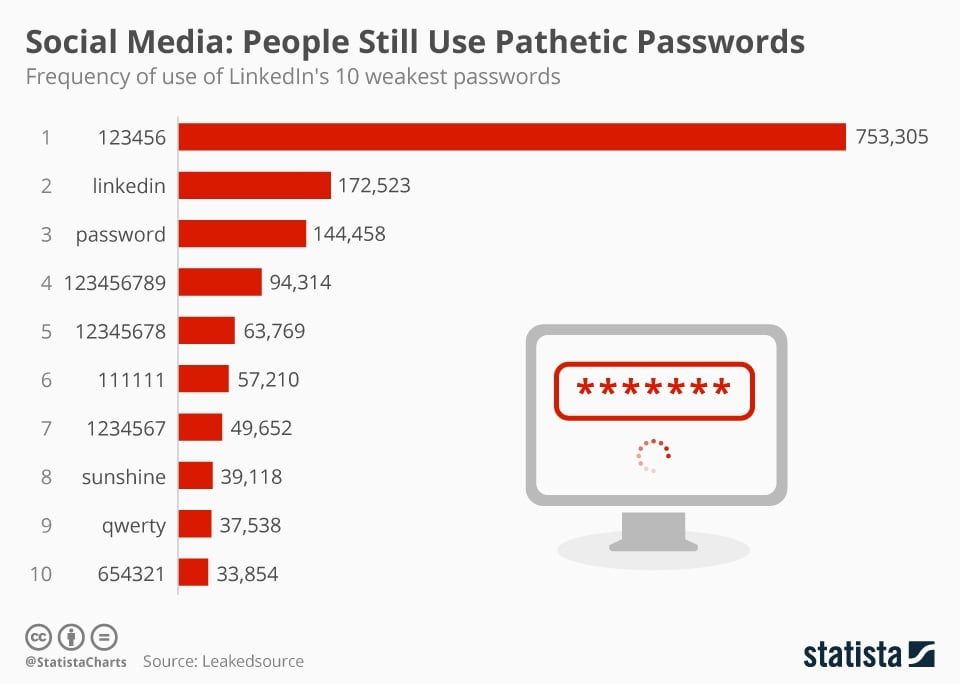
These Real World Data Breach Examples Will Make You Rethink Your Data Strategy

Data Breach Notification Congress Urged To Pass Law
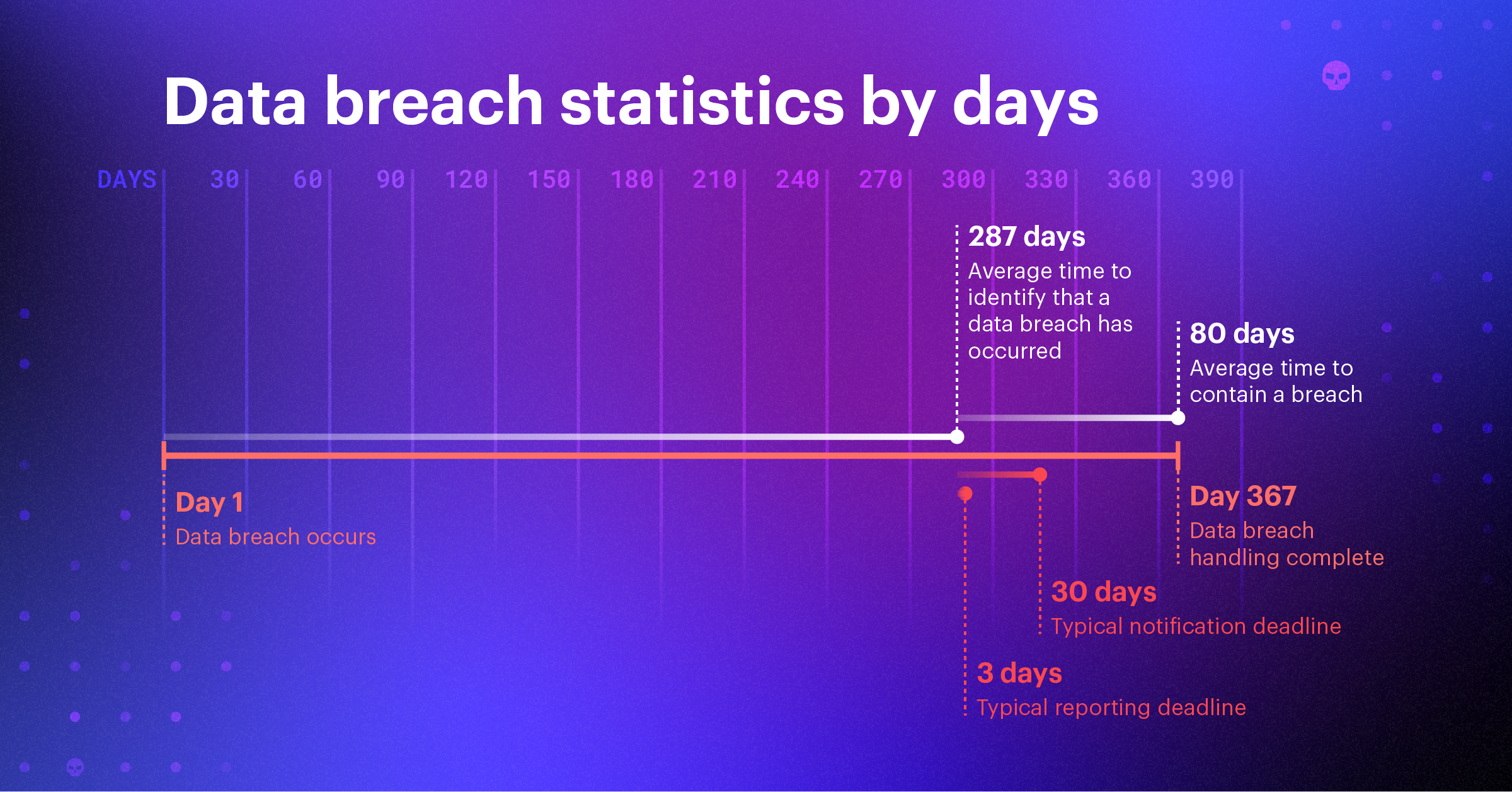
89 Must Know Data Breach Statistics 2022

75 Biggest Data Breaches Hacks And Exposures 2022 Update Termly
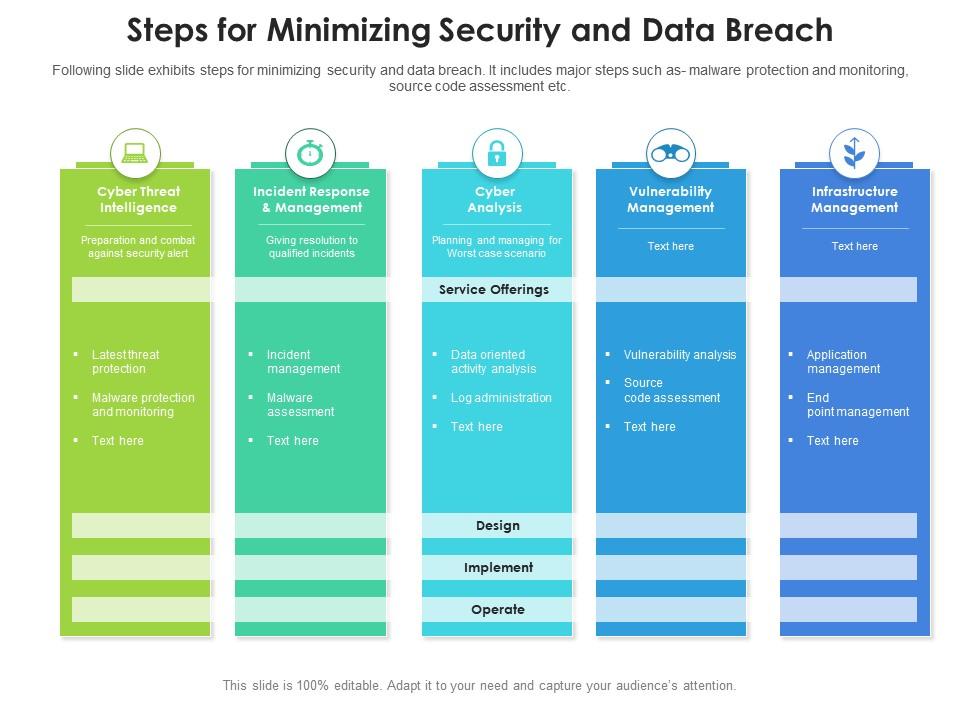
Steps For Minimizing Security And Data Breach Presentation Graphics Presentation Powerpoint Example Slide Templates

Reporting Personal Data Breach Under The Gdpr Data Privacy Manager
89 Must Know Data Breach Statistics 2022
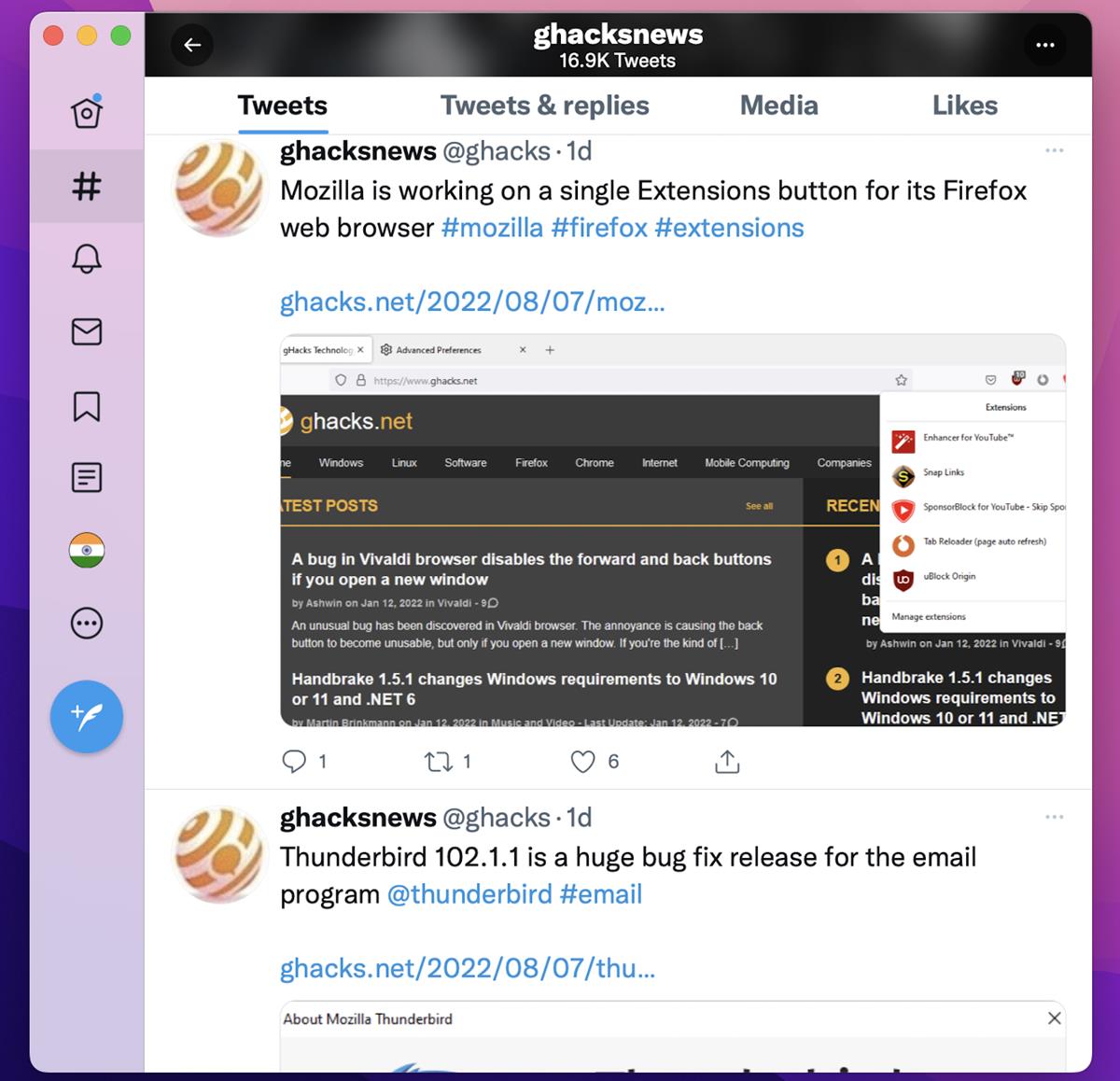
Twitter Data Breach Personal Details Of 5 4m Users Leaked
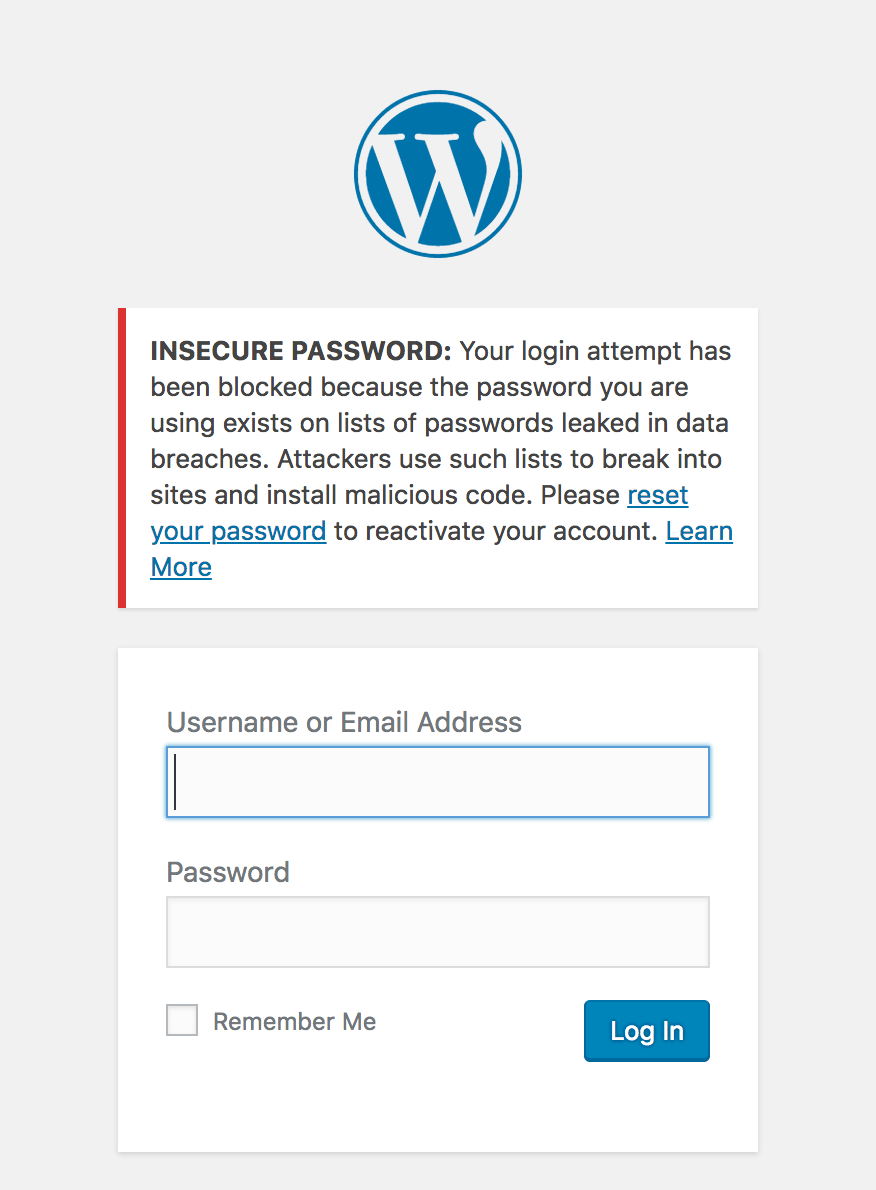
New Feature Protects Against Password Leak Attacks

Check On Data Breaches At The Privacy Rights Clearinghouse Journal Of Accountancy
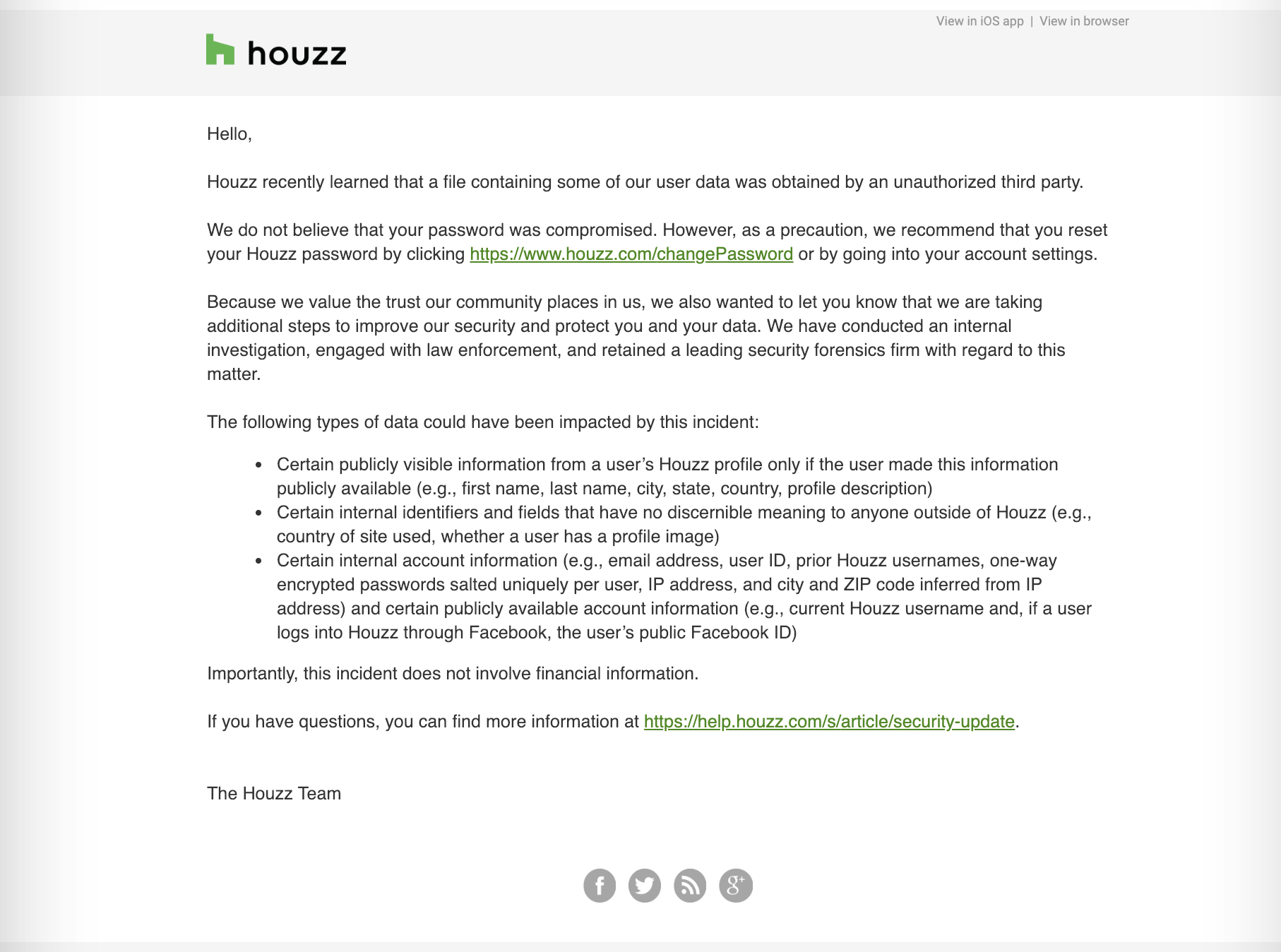
Houzz Resets User Passwords After Data Breach Techcrunch

Shell Data Breach Arnold Law Firm

Everything You Need To Know About Facebook S Recent Data Breach
